
Tim Nary, Chief Product Officer and Co-Founder at SnapAttack
Table of Contents:
What is going on in the SIEM market?
What are the implications for SIEM market customers?
What are the advancements and considerations in SIEM technologies?
Why is SIEM migration challenging?
The cybersecurity landscape is rapidly evolving, and nowhere is this more evident than in the Security Information and Event Management (SIEM) market. This period of transformation, marked by strategic mergers and high-stakes buyouts, signals not only a race for market dominance, but also the potential for profound changes in how cybersecurity solutions will operate in the future. As major players like Cisco, Palo Alto Networks, and various private equity firms maneuver for position, the implications for customers in the SIEM market are far-reaching, encompassing everything from technological advancements to operational challenges.
What's going on in the SIEM market?
The SIEM market is experiencing a wave of consolidation and strategic investments, aimed at expanding the capabilities of key players. This trend is driven by both financial and operational strategies, as companies seek to enhance their technological offerings and competitive positioning.
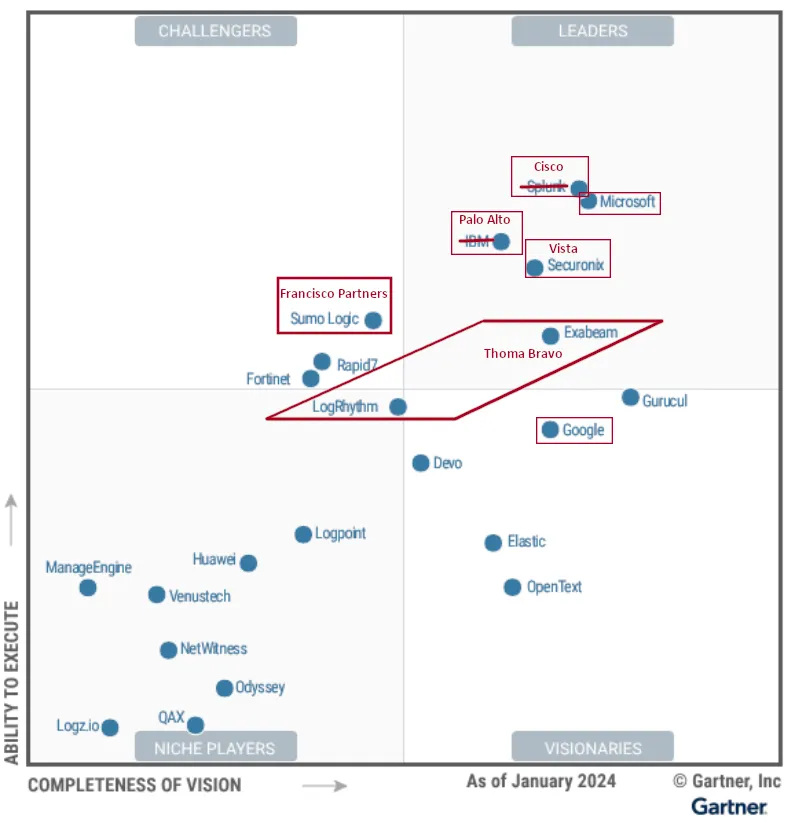
Platform Players
First, we have the Platform Players, which includes companies like Cisco, Palo Alto Networks, Google, and Microsoft. These platforms promise a seamless, integrated approach to cybersecurity, where all necessary tools are integrated and working together out of the box. Platforms simplify implementation and management, reducing both complexity and operational costs. They enhance visibility and centralized analysis, allowing for more effective threat detection and response through integrated threat intelligence and automation. Moreover, platforms offer cost efficiency by reducing the need for multiple vendor products and simplifying training requirements. They are also designed to scale with the evolving needs of organizations, supporting multi-cloud environments, hybrid work models, and emerging technologies, thereby ensuring future readiness. These benefits make platform players increasingly attractive to organizations seeking to streamline their cybersecurity efforts and strengthen their overall security posture. Cisco’s acquisition of Splunk and Palo Alto Networks’ acquisition of QRadar are significant moves that reflect the desire of larger companies to strengthen their cybersecurity portfolios.
Private Equity
Next, we have Private Equity, which include Thoma Bravo (LogRhythm and Exabeam), Vista Equity Partners (Securonix), and Francisco Partners (Sumo Logic). Their primary goal is to generate high returns for their investors, typically within a 3–7 year timeframe, then exit the investment through IPOs, sales, or other means to realize gains. Private equity often comes with a mixed reputation. On the positive side, they often provide significant capital and expertise to help companies grow and improve operations. They can streamline operations, enhance management teams, and focus on long-term strategic goals without the pressure of quarterly earnings reports, potentially leading to substantial improvements and growth in their portfolio companies. On the downside, PE firms often prioritize short-term financial gains over long-term stability. This can involve cost-cutting measures such as layoffs, heavy debt loading, and asset stripping, which may harm the company’s long-term health and its employees.
Up-and-Comers
Finally, we have what I’ll refer to as the Up-and-Comers. Interestingly, these aren’t obscure, niche players but well-known, publicly traded companies like CrowdStrike and SentinelOne. These companies are new entrants to the SIEM market with offerings such as Falcon LogScale (formerly Humio) and Singularity. Having already mastered the Endpoint Detection and Response (EDR) market, expanding to SIEM is a logical next step. This move allows them to unify data across cloud, endpoint, network, and other sensors, providing more comprehensive value for their customers. These up-and-comers can capture significant market share by offering their SIEM solutions to existing customers at little to no additional cost — your EDR data is already integrated, just add the rest.
What are the implications for SIEM market customers?
The consolidation and new entrants in the SIEM market have several implications for customers.
The trend towards creating integrated security platforms is becoming more pronounced. Customers can expect more holistic solutions that reduce complexity and improve overall security posture. As platforms continue to evolve, they will integrate seamlessly across SecOps workflows, effectively fusing threat intelligence, incident response, and other critical roles. This integration will streamline operations, enabling security teams to work more efficiently and cohesively.
The centralization of data is becoming more pronounced, and will lead to improved detection outcomes. Historically, many organizations have moved away from traditional SIEMs, citing issues like sluggish performance and high costs. While data lakes may reduce storage expenses, they often fall short in total cost of ownership (TCO) savings due to the additional resources required to operationalize them and overlay missing SIEM features. This gap has given rise to companies like Anvilogic and Hunters, which, despite positioning themselves as alternatives to SIEMs, essentially function as less-capable SIEMs built on data lakes like Snowflake, DataBricks, or AWS.
With centralized data, the industry is poised to unlock the true potential of AI. This isn’t another chatbot that analysts can query, but about advanced AI that can correlate events and anomalies across endpoint, network, cloud, identity, email, and other data sources. This capability, which XDR promised but failed to deliver fully, will transform how security operations function.
The SIEM market is making significant strides in addressing the gaps in automated response capabilities. Traditional SOAR solutions have struggled with seamlessly integrating and coordinating diverse security tools, often falling short in providing a unified, automated response to threats. These shortcomings include limited bi-directional connectivity with SIEM systems and challenges in handling big data analytics. However, future improvements are promising. Enhanced integration of AI and machine learning within SOAR platforms is expected to automate complex threat detection and response processes more effectively. This evolution will enable SOAR solutions to better leverage data collected by SIEM systems, streamlining workflows, and reducing manual intervention. Consequently, organizations can anticipate quicker, more accurate responses to security incidents, significantly bolstering their overall cybersecurity posture.
However, customers should be wary of the influx of buzzwords like “next-gen” in the market. While new entrants aim to match the features of established vendors while learning from their predecessors’ mistakes, the reality is that many of these innovations are still in their nascent stages. It is crucial to critically evaluate these claims, examining whether the proposed solutions genuinely meet your specific needs and if they can deliver on their promises. In a rapidly evolving landscape, it’s important to invest in technologies that not only fit current requirements but also have the potential to adapt and grow with future challenges.
Why is SIEM migration challenging?
You may find that your current SIEM isn’t meeting your expectations. In such cases, considering a migration to a new SIEM might be necessary. Evaluating your current system’s capabilities and comparing it with emerging solutions will help you make an informed decision about the best path forward for your organization. Migrating to a new SIEM isn’t without its challenges.
Regulatory requirements often mandate the retention of historical security data, complicating the transition to a new SIEM. This typically necessitates running both the old and new SIEM systems concurrently for a period, thereby increasing both costs and complexity. Even if security data can be successfully migrated to the new SIEM, it does not guarantee that detection capabilities will be equivalent or that analysts will maintain the same level of effectiveness. The learning curve and potential differences in how data is processed and alerts are generated can impact overall efficiency and effectiveness during the transition period.
Moving existing detections and dashboards to a new SIEM is often a manual, labor-intensive process. Organizations typically need to rebuild custom detections, dashboards, and reports from scratch in the new system. This effort is not only time-consuming but also prone to errors, and there’s no guarantee of functional overlap between the systems. Additionally, the process can disrupt normal operations, requiring significant resources and coordination across teams.
Why is now a great time to change SIEM solutions?
Despite the challenges, this is an opportune time to consider switching SIEM solutions. The SIEM market is highly saturated battleground, so companies looking to significantly grow their their market share can only do so by stealing customers away from their enemies. And they’ll do this by offering irresistible incentives for switching in this all-out war.
Palo Alto literally bought market share by acquiring QRadar from IBM, intending to migrate customers to their Cortex platform. But this migration isn’t without risks, as panicked customers are already eyeing alternatives. On-prem QRadar users may be wary of moving to the cloud-native Cortex XSIAM, but will suffer from a lack of innovation and receiving only minor updates to the legacy QRadar from IBM. In response, Palo Alto is partnering with IBM, training of over 1,000 security consultants on the migration, adoption, and deployment of Palo Alto products. But can this army of consultants and massive effort actually deliver the customers to Palo Alto?
This is the SIEM Wars — vendors are locked in a fierce battle for dominance. Splunk seems to have launched the opening salvo, providing “safe passage and a seamless transition path for IBM QRadar customers”, which includes either packaged discounts or up to one year of coverage of the cost for the Splunk solution, migration assistance, and training resources. The race is on, and the question is: who will be the next vendor to step up and join the fray?
Do you want to know more about the SIEM market?
At SnapAttack, we partner with leading SIEMs to help customers swiftly and effortlessly achieve superior detection coverage in their new SIEM environments. Our battle-tested process involves replacing legacy detections with equivalent or improved ones for the new SIEM, as well as migrating specific customer detections where gaps exist. But I am thrilled to announce that at Black Hat this year, we will unveil our new AI-powered SIEM migration capability. This cutting-edge technology will enable customers to more quickly and easily transfer their existing detections to their new SIEM, streamlining the migration process like never before
If you’re looking to elevate your detection and threat hunting programs or need assistance migrating to a new SIEM, reach out to us or book a demo to learn more about how SnapAttack can help.
For deeper insights into the SIEM Wars, join us at mWISE in September 2024, where you can catch my talk, “The SIEM Isn’t Dead: Comparing SIEMs and Data Lakes in Modern Cybersecurity.” Use code IM6KCMNW for discounted registration.
About SnapAttack: SnapAttack is an innovator in proactive, threat-informed security solutions. The SnapAttack platform helps organizations answer their most pressing question: “Are we protected against the threats that matter?”
By rolling threat intelligence, adversary emulation, detection engineering, threat hunting, and purple teaming into a single, easy-to-use product with a no-code interface, SnapAttack enables companies to get more from their tools and more from their teams so they can finally stay ahead of the threat.




