detection engineering
The world's most advanced detection engineering lab.
Eliminate the need for an advanced skillset to rapidly develop high-fidelity rules for the threats that matter most, and continuously deploy them via a purpose-built CI/CD pipeline.

Prioritize your most urgent detection blindspots.
Mobilize quickly with a structured detection development lifecycle.
Reduce false positives (AND negatives) and accurately assess coverage.
Detection engineering BEFORE and AFTER SnapAttack:
BEFORE
- You can’t easily identify detection gaps.
- Your best intelligence source is Twitter.
- You can’t keep up with the barrage of latest threats and don’t know where to prioritize.
- You don’t have a good way to test and tune detection logic.
- You’re drowning in noisy alerts, but testing and tuning is challenging and cumbersome.
- You don't have the skills in-house to develop your own detection content.
Your detection engineering strategy is ad-hoc, reactive, and driven by external priorities (AKA the headlines).
AFTER
- You have a clear picture of your detection coverage (and gaps).
- You have an agile process that enables you to quickly develop and deploy detections for the threats that matter most.
- You feel more confident with built-in feedback loops and automated validation.
- You’re equipped to keep up with new and emerging threats.
- You can continuously assess, tune, maintain, and improve coverage.
- You can rapidly and efficiently develop detection content with the people you already have.
Your detection engineering strategy is faster, more reliable, and focused on your organization’s real priorities.
the threats that matter
Stop struggling to figure out what matters.
Start understanding what to prioritize, where to begin, and how to quickly deliver coverage to your SOC.
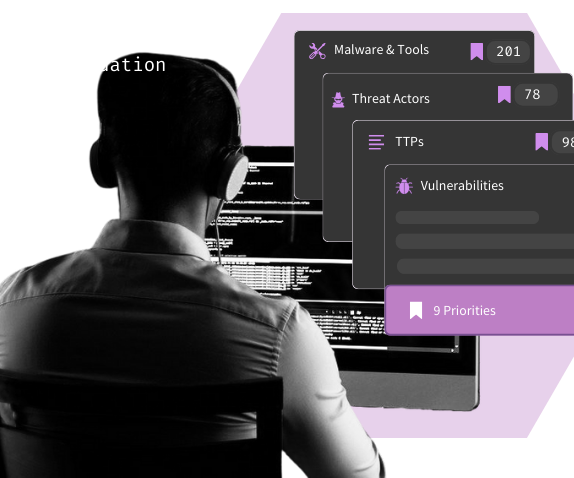
Determine the threats that matter with Threat Profiles
Discover where you have detection gaps based on factors like your industry, tech stack, region, risk threshold, and more.
Visualize attacks from the adversary’s lens, risk-free with our Attack Library
Understand the attack from all angles, leveraging our threat research (3,000+ attacks) or supercharge your own with our Sandbox and ML.
powerful detections, faster
Stop bogging down your SOC with noisy rules.
Start developing high-fidelity detections with the velocity and precision your SOC demands.
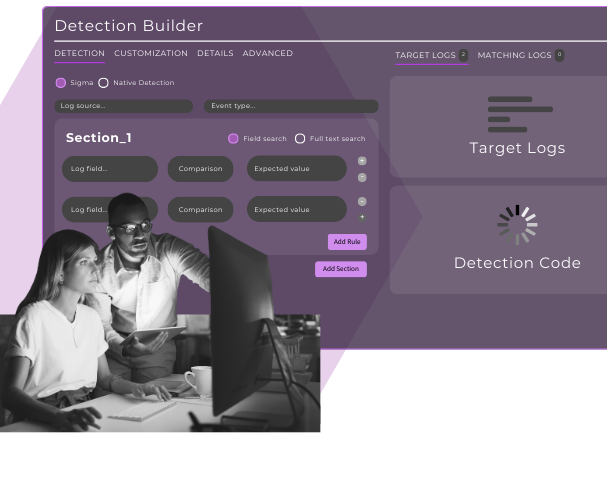
Shortcut development with our Detection Library
Get a jumping off point on detection development with our library of 10,000+ pre-built, validated, high-confidence alerting rules and let our ML help you customize them...or just press “go”.
Build, test, and tune with our No-Code Detection Builder
No code? No problem. Build detections in any query language, test their performance, and tune them as needed all from our Detection Builder - powered by machine learning (ML) trained on millions of true positive logs.
and validate with ease
Stop wondering if you’re protected due to disconnected, incomplete feedback loops.
Start taking a results-driven approach to the detection development lifecycle.
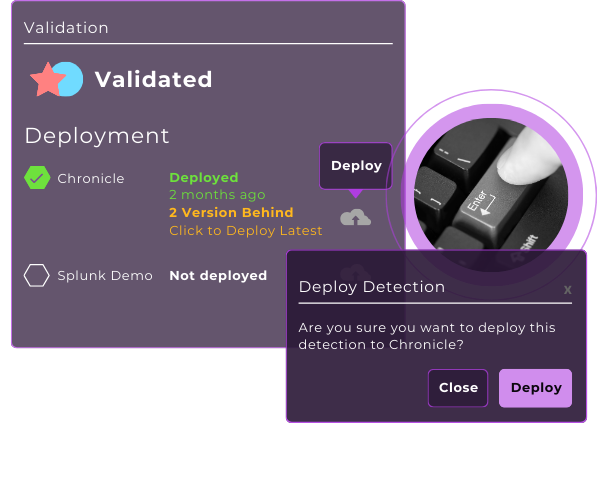
Reduce alert fatigue - and missed alerts - with Confidence Scoring
Don’t blow up your SOC by taking a risky guess on your alerting rules. Confidence Scores on each detection predict false positive rates for you and tell you exactly how the rule will perform - even before you deploy it - giving you clarity and assurance in your coverage.
Prove your detections work with the Validation Engine
You know a pen test once a year isn’t enough. Close the loop on the detection development lifecycle by proving your coverage will work when it matters most.
Have your security teams work smarter, not harder.
Case Study:
Empowering In-House Cybersecurity Excellence at a Fortune 500 Bank
why snapattack?
We built the world's most advanced detection engineering lab so even under-resourced and junior teams could operate like the world's most advanced detection engineers.
SnapAttack was designed to break the barriers of traditional threat detection tools. Here’s what we can promise you:

Fast time to value.
Get more from your teams and more from your tools with built-in training and 30+ direct integrations.
Try before you buy.
We want to make sure we’re a good fit. That’s why you get a POV that reflects your unique environment before you sign off on ANYTHING with us.
Easy to use, easy to scale.
Cybersecurity is for everyone - that’s why SnapAttack is easy for even junior analysts to navigate with built-in training to keep up with your team’s skillset as you grow.
Expert support at your fingertips.
Our customer success and product teams are available via Slack and regular check-ins to make sure you’re getting everything you need out of our platform.





















With over 30+ direct integrations with the most common SIEM, EDR, or XDR tools, SnapAttack makes one-click deployment simple. And, we’re adding more every day. If you don’t see your tools here, let’s chat. Explore integrations >

Security Engineering Leader at a Large Data Center Provider
services
Whether you're trying to build a detection engineering team, take yours to the next level, or put it in the hands of experts, SnapAttack can help.
Detection Engineering Maturity Assessment
Ensure your detection engineering strategy maps to your unique alerting priorities and measurably improve your program’s maturity.
Find out where your detection blindspots lie and how you can proactively, continuously ensure that you’re protected.
MITRE ATT&CKTM Assessment
Few companies know where their MITRE ATT&CKTM technique coverage stands…and without it, they can’t tackle their urgent security gaps.
Identify your blindspots and the actions you need to take in order to get them covered, with expert guidance and dynamic measurement.
Detection Engineering as-a-Service
Some organizations don’t have the bandwidth to perform detection engineering in-house, but that shouldn’t hold you back from proactive defense.
Let our experienced team of detection engineers detect and shut down your most critical threats, without any extra effort from you.
Ready to get started with SnapAttack?
Here's how it works:
step 01
Demo + discovery
step 02
No cost, no obligation proof of value
step 03
Start detecting the threats that matter, faster
Fast + easy deployment
Tailored to your goals, processes, and tools
Complimentary reporting included
Flexible, customized, hands-on support
resources
Unlock a proactive detection engineering strategy with our popular resources:
And see how it’s done in our Threat SnapShots:
explore our other use cases
threat hunting
Proactively reduce risk across your attack surface – even within large, decentralized environments.
threat intelligence
Operationalize expert threat research that’s actually relevant to your organization.
siem migration
Prioritize, expand, and report on MITRE ATT&CKTM coverage, without the alert fatigue.
explore our other use cases
threat hunting
Proactively reduce risk across your attack surface – even within large, decentralized environments.
threat intelligence
Operationalize expert threat research that’s actually relevant to your organization.
siem migration





