Adversary’s Arsenal – T1053: Scheduled Task/Job

Table of Contents: Introduction > Recent Relevant Intel > Methods of Execution > Persistence > Privilege Escalation > Lateral Movement > Impair Defense > Click here to watch “Adversary’s Arsenal: T1053” on YouTube > Introduction New and emerging threats may get the headlines, but if they’re all you’re focused on, your defense is hardly […]
Leading Global Data Center Provider Accelerates SIEM Migration and Improves Threat Coverage with SnapAttack

DOWNLOAD NOW > When a leading data center provider approached SnapAttack about a SIEM migration, they were on a rapid timeline to not just maintain but improve their threat coverage – challenges common to a cumbersome SIEM migration. SnapAttack offered a vast and threat-informed detection library, simplified integration with the target SIEM, and automated validation […]
Modernizing Threat Intelligence with TTPs: Not Your Father’s Threat Intelligence Pt. 1

TL;DR: Think differently about threat intelligence with TTPs.Traditional approaches to threat intelligence leave security teams reactive, overwhelmed, and unable to quickly and proactively address threats. Operationalizing TTP-based intelligence carries some challenges, but the juice is well worth the squeeze. Table of Contents: All About the Pyramid of Pain Traditional Threat Intelligence: IOCs and Finished Intelligence […]
Senior Account Executive

Remote | Our Senior Account Executives are key individuals who prospect, maintain, and expand relationships with accounts in assigned territories. You will be responsible for the full sales cycle including outbound prospecting, building pipeline, and closing business. We are looking for Account Executives with an ego drive and a hunter mentality, consultative selling approach with our customers and channel partners.
Senior Solutions Architect

Remote | Our Senior Solutions Architects are key individuals who enable sales success through deeply understanding our customer’s challenges and SnapAttack’s unique value propositions. You will be responsible for supporting our Account Executives with technical subject matter expertise clearly articulating to customers the security benefits realized by engaging with SnapAttack. We are looking for Solutions Architects with an expertise-driven consultative selling approach with our customers and channel partners.
Mandiant Threat Intelligence & SnapAttack for Enterprises, a Better Together Story: Enhancing Your Detection Engineering Workflows

Detection engineering is the process of creating, testing, deploying, and maintaining detections that alert security teams to malicious activity in their environment. Detection engineering is a critical component of a threat-informed defense, which is a proactive approach to cybersecurity leveraging threat intelligence, attack emulation, and behavioral analytics to improve security posture and reduce risk. However, […]
What’s Holding You Back? A CISO’s Perspective on Proactive Security

Paul Caiazzo, former CISOand current Chief Growth Officer at SnapAttack Linkedin Table of Contents: What is Proactive Cybersecurity? Benefits of Proactive Security What Holds Organizations Back From Being Proactive? How Can Organizations Enhance Cyber Maturity and Achieve Proactive Cybersecurity? Everyone wants to achieve “proactive security” right now. There’s not a tool on the market that […]
Threat Researcher

Remote | In this unique hands-on research role, you’ll follow the latest cyber threats and industry trends from open source and customer intelligence, replicate cyber attacks and add them to our threat library, and create high quality behavioral detections to defend our customers. You’ll have the opportunity to interact with the community and share your research through blog posts, videos, webinars, and speaking at industry conferences.
SnapAttack’s Threat Hunter’s Workbench: Revolutionizing Cybersecurity with Advanced Threat Hunting and Detection

In today’s rapidly evolving digital landscape, the battle between cyber attackers and defenders has reached new heights. Cyber threats have become more sophisticated, targeting organizations of all sizes and industries. To stay ahead of these threats, organizations require innovative and powerful cybersecurity solutions that empower their security operations teams to proactively hunt down and detect […]
Continuous Threat Exposure Management (CTEM): A Proactive Cybersecurity Model
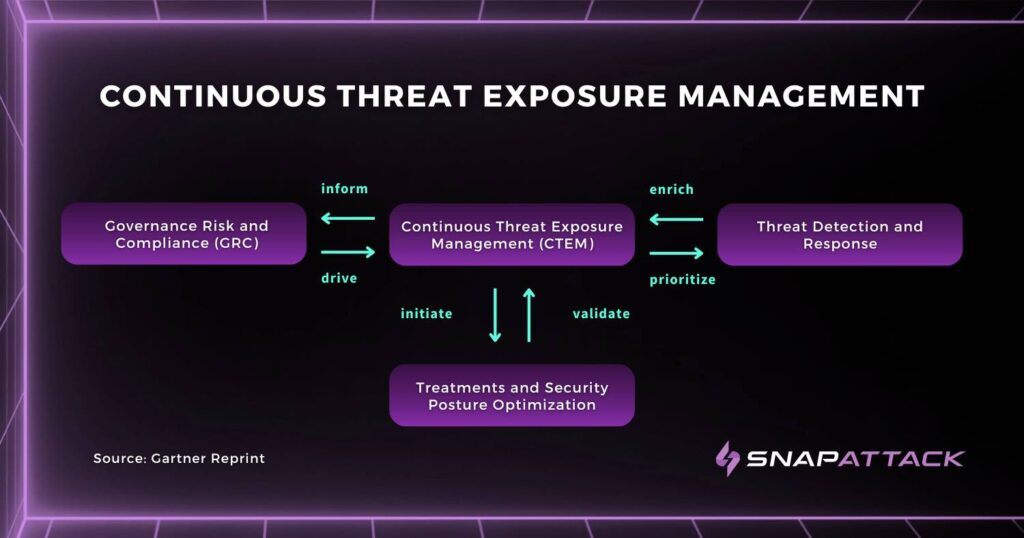
At any given moment on any given day, are you able to confidently answer the question, “Are we protected?” If you’re testing your security controls any less often than every single day, the answer to that question is a hard – and stressful – “no”. In the history of human technology, we’ve never had access […]
