TL;DR: Think differently about threat intelligence with TTPs.
Traditional approaches to threat intelligence leave security teams reactive, overwhelmed, and unable to quickly and proactively address threats. Operationalizing TTP-based intelligence carries some challenges, but the juice is well worth the squeeze.
Who Built The Pyramids? The Pyramid of Pain, IOCs, and TTPs
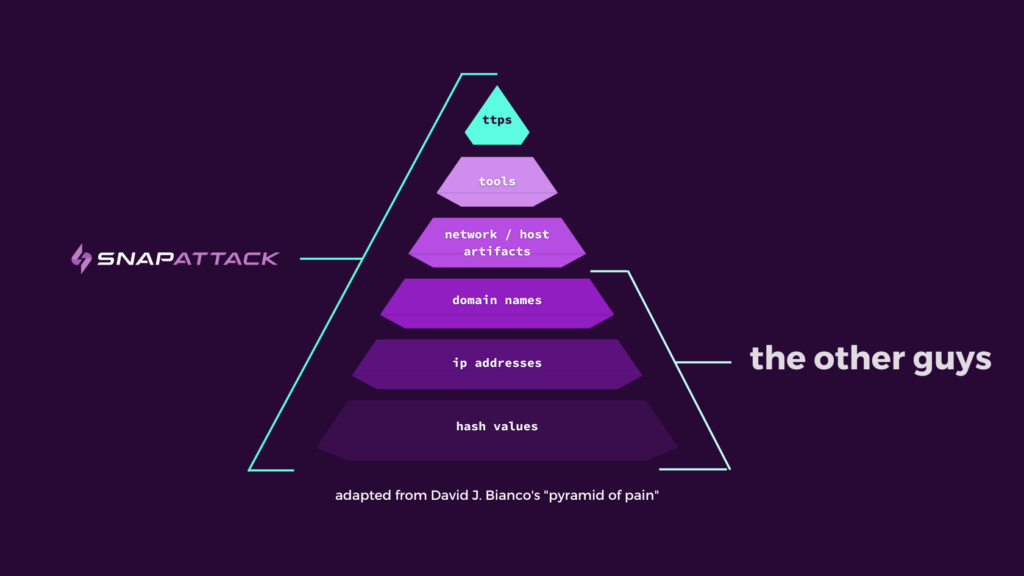
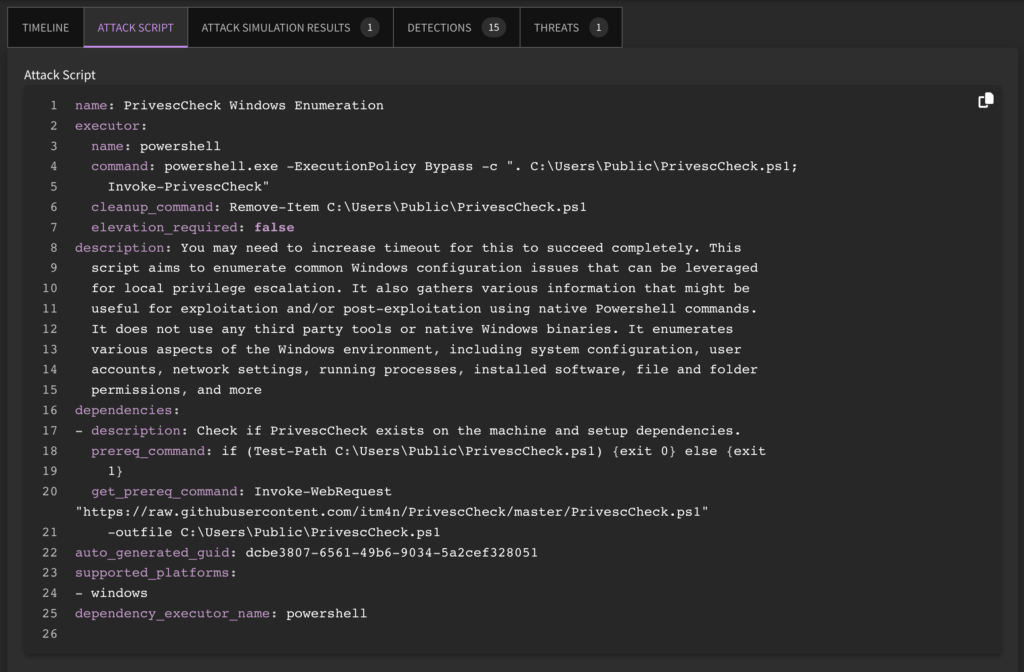
So those at the top of the Pyramid? They’re leveraging TTPs (Tactics, Techniques, and Procedures) to both catch threat actors in the act AND predict malicious activity before the alarms go off.
Traditional Threat Intelligence: IOCs and Finished Intelligence
Indicators of Compromise (IOCs)
Indicators of Compromise (IOCs) include:
- Hash values
- IP addresses
- Domain names
- Network / host artifacts
Finished Intelligence
These organizations tend to have complex attack surfaces, low risk appetites, and threat models that include sophisticated and dangerous adversaries, and they know that an IOC feed – no matter how good – is just one element of an effective intelligence strategy.
Challenges with Traditional Threat Intelligence
Challenge #1 – Information Overload: It’s impossible to sift through the noise or contextualize alerts when you don’t know what to look for. Traditional IOC feeds aren’t tailored to the user’s environment or, more importantly, threat landscape. Even with good automation, teams struggle to sift through ALL of the threat intelligence available to them – making it nearly impossible to figure out what’s actually helpful.
Challenge #2 – Stale Data: So you’ve got a mountain of threat intelligence in front of you – what next? Depending on your sources, the quality of the data could be the next challenge to overcome. Since adversaries can so easily change infrastructure, indicators like IP addresses and domain names have a very short shelf life.
If you’re alerting based on stale IOCs, not only are you consuming precious cycles reacting to false positives, you’re probably blind to a lurking false negative problem, too. It’s all well and good to blacklist or alert on known-bad IPs or domains, but the strategy proves fragile the moment that attacker moves their command and control infrastructure and the attack sails by your defenses.
Challenge #3 – Cha-Ching: Quality finished intelligence is typically reserved for well-funded organizations. Not only is the service costly (if you want to reap any real benefits, that is), but the organization must also invest in intelligence analysts to interpret the information.
For most organizations, this level of expense is untenable; the team they already have is expensive enough and they’ve sunk costs into an extensive toolkit already. They’re not jumping at the chance to tack on a few more zeroes to their security spend.
Challenge #4 – Checking a Box: Threat intelligence has been around for a long time, and pretty much every CISO in the world knows they need something. There’s also a common misconception that “threat intelligence=IOC feed”, because that’s the easiest place to begin and there are a wealth of free sources that aren’t going to consume precious budget.
Whether it’s to save time, money, or manpower, many companies get an open or closed source IOC feed plumbed into their firewall or SIEM, and consider that the end of the road. In other cases, the firewall or SIEM vendor includes a basic feed as part of the platform and many think that means they’re covered. Spoiler alert: they’re not.
Challenge #5 – Actionability: Rather than looking ahead to unknown threats, IOCs and intelligence feeds tell you what’s already happened to someone else – making them significantly less helpful in building a proactive, preventative security strategy.
And since many intelligence teams lack the technical skill required to set their detection engineer, SOC analyst, incident response, and threat hunt colleagues up for success, the baton-passing from intelligence to ops is cumbersome, or at the very least not specific enough to incite any action.
IOCs vs. TTPs: What’s the Difference?
Make no mistake, you should certainly hunt with fresh IOCs after a major zero day is announced – recency is a key indicator of quality in the case of IOCs. Against some campaigns, IOCs have been and will continue to be key to preventing many incidents. But if your intelligence program is over – or solely – reliant on IOCs, you’ll find yourself in a never-ending game of IOC whack-a-mole, because the adversary is no longer where you thought they’d be.
What Are TTPs?
Tactics describe the overarching goal a threat actor has when conducting an attack.
Techniques are the methods and tools attackers use to achieve tactics.
The MITRE ATT&CK® Framework has become the industry-standard reference for adversary behaviors, and can be incredibly useful both in better understanding an attack as well as measuring one’s existing coverage and visibility. By helping organizations understand what an adversary seeks to accomplish and how they may do it, MITRE ATT&CK® gives intelligence teams both more insight and an action plan when they hand findings off to operations.
Benefits of TTPs
More sophisticated threat intelligence leads to more sophisticated threat detection. TTPs are proactive, indicative of an attacker’s likely next steps, and challenging (if not impossible) for threat actors to alter.
Benefit #1 – Resilient Detection: By keying in on the actions an adversary may take rather than a list of known-bad IPs, your detection strategies become more robust, and are able to survive the inevitable cycle of new malicious IPs, domains, and hashes. You’re much less likely to suffer false negatives.
Benefit #2 – Context-Led Prioritization: TTPs help teams identify attackers’ methods and motivations, which means they can get to the core of WHY and HOW an attack may occur. Organizations can proactively allocate resources towards likely exposures and implement defenses rather than recover afterward.
Benefit #3 – Proactive, Threat-Informed Defense: Whereas IOCs can only help you identify known threats previously seen in an attack, TTPs go the extra mile and enable you to uncover unknown threats. Teams that hunt using TTPs take a proactive stance and can actively prevent lurking threats from damaging their organization.
Even if the threat actor has already gained access to an environment, a team hunting with TTPs is significantly more likely to have the ability to prevent an adversary from progressing along an attack chain and accomplishing their objective (ransomware deployment is a great example).
Benefit #4 – Patterns of Attack: With a broad, comprehensive view of specific adversary behavior, organizations are better able to understand the sequences of events that are likeliest to be leveraged against them. Moving forward, they’ll know exactly where to prioritize detection engineering and threat hunting, and ultimately, how to get ahead and thwart an attack.
Challenges to Leveraging TTPs
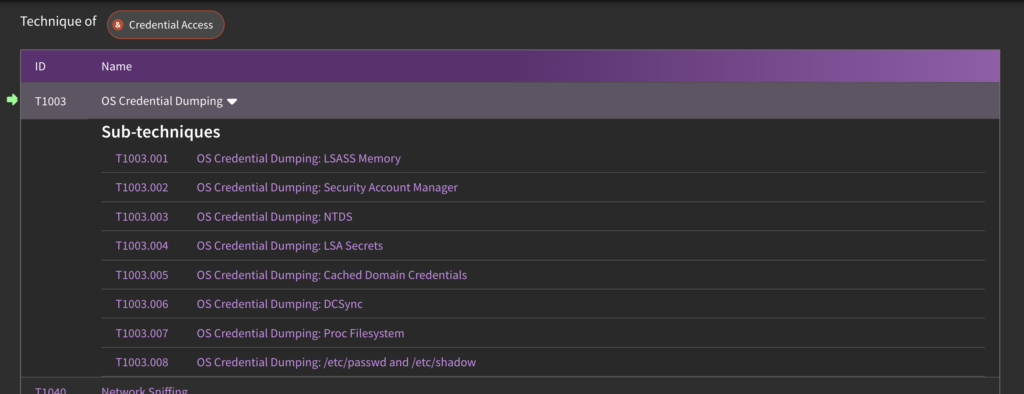
Challenge #1 – Specificity and Depth of Coverage: While intelligence on a given adversary’s preferred technique is incredibly valuable, that alone may not be specific enough to build and execute an effective detection strategy. MITRE ATT&CK ID T1003 – OS Credential Dumping is a great example of this conundrum.
OS Credential Dumping is a technique with 8 subtechniques, meaning there are at least 8 unique ways an adversary may be able to compromise credentials via this technique. Moreover, within SnapAttack, we’ve captured no less than 187 different variations of this technique. In some cases, detection strategies are robust enough to catch multiple sub-techniques and their variations, but in others, they may not be.
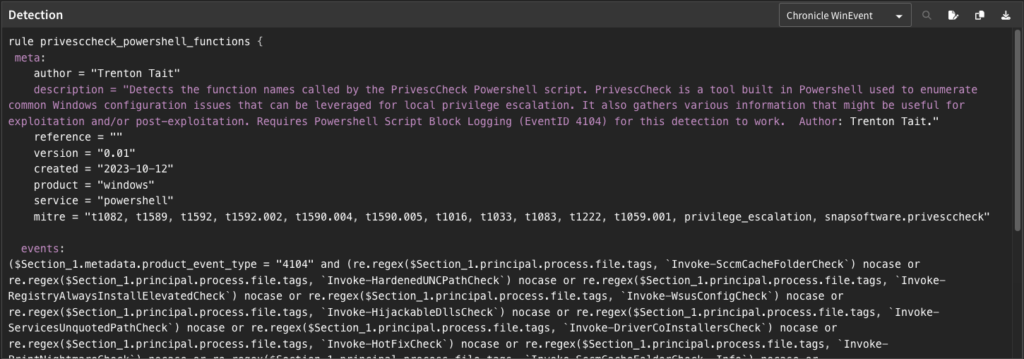
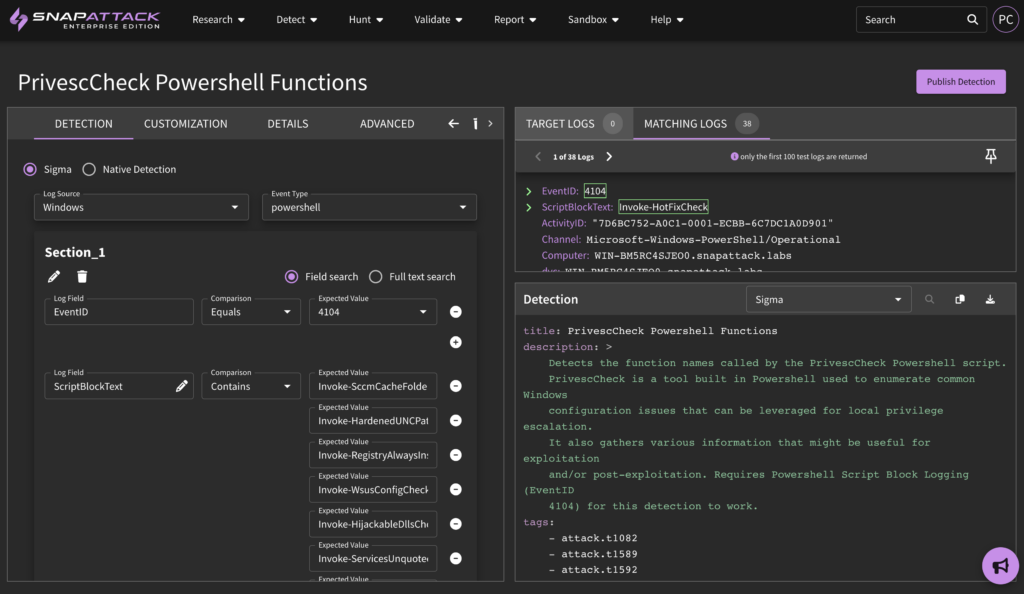
Challenge #2 – Detection Engineering Skills: Building upon the last challenge, once a security team knows the techniques and subtechniques they’re focused on, they need to build the actual detection logic that will be used to identify the adversary’s activity. While this sounds simple, it can be incredibly complex, as it requires a deep understanding of the technique, the data available to the threat detection team in its detection tools (SIEMs, EDRs, XDRs and datalakes), and the query languages each tool in their environment uses.
Challenge #3 – Adversary Emulation: In order to build reliable detection logic, you need a deep understanding of the attack and the evidence it leaves behind. The best way to accomplish this is adversary emulation, but adversary emulation requires a blend of skills across infrastructure, offense, and threat detection – not to mention an environment within the organization suited to the activity of safely executing malicious actions. Not every organization has the ability to fulfill these requirements, and without them, they risk running ineffective or poor-performing detection logic, resulting in either high false positives, or worse – false negatives and incidents.
Using TTPs for Better Threat Detection
Specificity and Depth of Coverage: Fighting bad actors on a wide attack surface that’s only growing has led many security teams to think that the more alerting rules they’re running, or the more IOCs they consume, the safer they are. But all that leads to is a false sense of security and a needlessly noisy SOC.
That’s where both breadth and depth of coverage are crucial: when security teams know which TTPs are specifically relevant to their environment, they can more quickly, effectively, and proactively implement the measures / deploy the detections needed to protect against them.