Even though proactive security is all the rage, it seems like few companies actually understand what it is and have successfully achieved it. So what does a truly proactive cybersecurity posture look like – and why do security teams struggle so much to get there?
In short, security is proactive when the team is prepared to identify, prevent, and detect attacks instead of responding to and recovering from them (whenever possible). To do that, they need:
These are the core tenets of a successful, proactive security environment – but they’re also indications of a truly mature cybersecurity program.
To achieve a proactive, mature posture, what teams need most of all is time – the hardest asset to come by in a SOC. Because they’re slammed with false alerts, constant fire drills, and ineffective toolkits, reactive security is the reality for most companies. They lack the time, tools, and resources to be proactive, and thus are forced to focus on known threats and incident response initiatives, rather than looking ahead to the unknown to protect themselves.
Many organizations are hesitant to take the jump from reactive to proactive because they see it as a hefty investment of resources, or they simply don’t know where to start. But investing the time, money, and brainpower to build a proactive cybersecurity program returns a much higher ROI than recovering and responding to events as they occur, time and time again.
Proactive security is the gift that keeps on giving. Many companies are held back from achieving preventative cybersecurity because they’re operating with inefficient processes in noisy SOCs. But when you pursue a proactive cybersecurity posture, you can kill two birds with one stone.
Being proactive requires an awareness and sensitivity to your organization’s environment and security standing. That means you have to know which threats are most likely to hurt you, where your weaknesses are, and where you can count on your defenses to keep you covered. The thing is, these things change all the time. Environmental drift is real, so to stay proactive, you have to maintain a thorough, dynamic understanding of the context in which you’re operating.
When you have comprehensive, up-to-date knowledge of your security posture, you know where it’s wisest to invest your time and resources. That’s why proactive cybersecurity teams see the rewards of continuous improvement – they know what they need and have the time, space, and resources to achieve it.
Security teams across the world all seem to understand: proactive security is the best security. Why aren’t more of them actually practicing it?
Most organizations are operating right-of-boom – right off the bat, many companies struggle to prepare for incoming threats. There could be a multitude of reasons for this. Maybe they lack funding. Maybe they have the funding, but they’re forced to spend it on band aid solutions to incidents. And maybe they have the potential to be mature enough, but they haven’t found the time to make that a priority.
A mature organization will prepare for potential attacks through threat modeling. Effective threat modeling identifies risks, evaluates vulnerabilities, contextualizes relevant threats, and helps teams prioritize moving forward. Unfortunately, when immature organizations practice threat modeling, they don’t achieve the same results.
They rarely follow through with the risks they’ve identified, stopping once they’ve consumed indicators of compromise (IOCs). And while that bare minimum may provide some level of protection, when sophisticated threat actors like nation-states almost never reuse IOCs, that can yield a false sense of security that does the organization very little good.
For a real-world example that applies to security teams everywhere, think back to Log4Shell. In nearly every organization, simply understanding potential exposure was an incredibly challenging task because the vulnerable code was baked into applications throughout the enterprise. In many cases, no patch was immediately available, taking the organization’s fate in many ways out of their hands.
In situations like that, while the goal of patching is ever-present, it’s critical to understand where and how to apply compensating controls that minimize potential exposure. In this way, a detective control to identify potential exploitation of an unpatched vulnerability is a critical element of proactive security. Log4Shell isn’t the only example of this – security teams everywhere should be thinking of threat detection as a means of buying the vulnerability management team time to comprehensively do their job.
Even when updates are in your control, the challenges of proactively managing your exposure are myriad and constantly changing. The practice of Continuous Threat Exposure Management (CTEM) was born from the need to address these challenges, and organizations seeking to achieve a highly resilient proactive approach to security are investing in the tools, processes and people to enable it.
It takes a lot of time and money to find and configure tools that combat your relevant threats in your unique environment…time and money that immature organizations just don’t have. And when you’re working off of a rocky foundation like that, it’s really hard for the rest of your security strategy to catch up.
In many ways, it may seem counterintuitive to consider threat detection an element of proactive security as it naturally aligns to the identification of malicious activity that is occurring in the network, meaning prevention has already failed. What this overlooks is that breaches aren’t instantaneous forces of nature that suddenly appear.
Every company spends money on a SIEM or EDR (probably a lot of money), but those tools aren’t effective out-of-the-box. If they aren’t set up according to the specific vulnerabilities in their given environment, organizations will be bombarded with false alerts that don’t truly apply to them. As a result, they won’t know which logs to monitor, which threat actors to look out for, or which detections to deploy.
Even when those challenges are solved, most organizations still take a reactive approach to threat detection – they build the telemetry data pipelines and configure their detection tools, and wait for alerts to triage. While this might work for known threats, it lacks the proactivity that active threat hunting yields.
Proactive threat hunting requires a level of maturity many organizations have yet to build. Obstacles around threat modeling, detection engineering, triage and analysis exist that may depend on expertise or tooling the organization lacks. Investment across the proactive disciplines described earlier unlocks opportunities in threat hunting that dramatically reduce the organization’s exposure.
If there’s one common theme that unites the challenges holding organizations back from maturing, it’s that cybersecurity maturity relies on a thorough and contextually-driven foundation. So how do teams achieve that?
Teams need workflows and tools that empower them to collaborate towards a common goal. When each team’s findings and output inform other members of the SOC, they’re so much stronger than the sum of their parts.
Remember the threat modeling we talked about earlier, and how many organizations either don’t use it effectively or don’t do it at all? That’s the starting point for a good CTI program, and where so many organizations go wrong. It’s what keeps them on track, and without it, they fly off the rails completely.
Threat modeling identifies variables that the security team needs to consider as they develop and enhance their defenses – variables like:
By tracking those kinds of characteristics and metrics, analysts can produce threat intelligence reports that equip different teams to take appropriate action. A well-formulated and maintained threat model allows the CTI team to tailor their outputs – strategic or tactical intelligence – to each of the intelligence team’s customers.
Intelligence customers include vulnerability management, incident response, threat detection, even GRC – and each has unique needs for relevant intelligence.
Some questions you can ask yourself when analyzing cyber threat intelligence are:
By answering these questions before attempting to put your threat intelligence to the test, you can avoid the headache of sifting through irrelevant data and trying hopelessly to extract some value out of it. Threat intelligence can make or break your security posture – make your tools work for you, not against you.
Learning how to leverage threat intelligence sets a strong foundation for my final recommendation, which might be an obvious one: be proactive.
You have to identify and address threats as early as you can, because if you don’t, they’ll get to you first. Once you’ve done the work to design an impactful, contextualized CTI program, you can expand your focus to prevent threats instead of simply responding once you’ve already been attacked. You can assess gaps in your coverage and test your defenses before a live adversary tests them for you. You can finally get ahead of the threat.
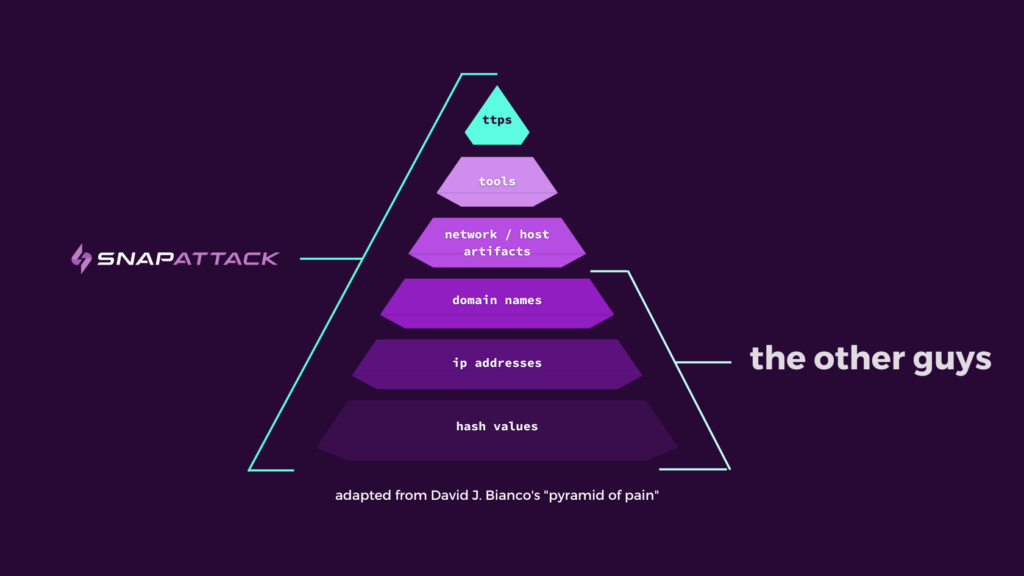
TTPs and behavioral indicators are harder for threat actors to change, meaning a focus on identifying behavior is much more resilient than focusing on IP addresses, hashes and domain names. In addition, you can only find IOCs if the attacker happened to slip up somewhere along the way…but you can identify TTPs even if the attacker executed a “perfect” attack.
By analyzing behavioral indicators of attacks rather than historic data like IOCs, you can then incorporate those more proactive measures into the rest of your security strategy. Proactive threat intelligence leads to proactive threat hunting, threat detection, detection development, and so much more. It helps CISOs invest in the right tools. It helps threat hunters avoid wild goose chases. And it helps detection engineers build more powerful, relevant detections.
It might be cliche, but context is king when it comes to threat detection and a robust security strategy. Context is the foundation of everything a SOC needs to be successful – and as we’ve covered, a strong foundation equips security professionals to enhance and advance their defensive strategy.
I’m a former CISO, threat hunter, and just about everything in between…at SnapAttack, our whole leadership team is. We know the challenges that today’s security teams face because we’ve been there, too. We want to remove the barriers to proactive threat management and help today’s teams overcome the hurdles in their way – the hurdles placed in front of them by an oversaturated tool market, a complex threat landscape, and outdated detection and remediation processes.