
What is Threat Hunting? And Why Are Threat Hunters in Such High Demand?
According to Splunk’s 2023 State of Security report, the median time from compromise to detection is nine weeks. Mandiant’s 2023 M-Trends report clocks median dwell time at 16 days. Either way, both numbers are FAR too high – and the damage a hacker can do in that amount of time can be devastating.
Enter threat hunting as a solution to tracking down hidden hackers. Proactive threat hunting is a framework in which hunters actively search for lurking threats before attackers have the chance to strike. Threat hunters analyze large volumes of data, study network activity, and leverage threat intelligence along with other threat detection tools to mitigate threats before they become a full-blown crisis.
Sounds great – so what’s the catch?
Threat hunting is an advanced cybersecurity discipline that requires years of experience, a deep understanding of complicated tools, and its own language of complex terminology. It’s neither a quick nor easy fix to hire advanced personnel in today’s cybersecurity talent gap – skilled threat hunters are few and far between. Threat hunting is an art that takes time, resources, skills, manpower, and funds that a lot of security teams just don’t have.
The good news?
Just because it’s difficult to find or train a threat hunter for your team, doesn’t mean it’s impossible. Upleveling a junior analyst to a threat hunter might seem daunting – but in a slippery job market with a widening skill gap, it’s one of the most worthwhile investments security leaders can make for their teams.
When you’re looking to add a threat hunter to your security team, it’s best to start with the basics. So where do you begin?
Cyber Threat Hunting Terminology
Cybersecurity professionals have developed somewhat of their own vocabulary – below are a handful of terms that threat hunters will need to know in order to communicate with their team members, leadership, and peers.
Indicators of Compromise (IOCs): IOCs are pieces of evidence that hackers leave behind after an attack. Examples of IOCs are:
- Hash values
- IP addresses
- Domain names
Searching for IOCs is like dusting for fingerprints – they may help you find the culprit, but they won’t tell you where they’ve gone or prevent the damage that’s already occurred.
Indicators of Attack (IOAs): IOAs are more like the sound of tires screeching as the adversary drives the getaway car. They’re happening in real-time, and they tell you what the adversary is doing in that given moment.
You can follow them. You know where they’re going, and you know what to look for. And best of all, you can shut the adversary down before the damage is done.
Examples of IOAs are:
- Network artifacts
- Lateral movement
- Exploited credentials
- TTPs
Tactics, Techniques, and Procedures (TTPs): TTPs are a subset of IOAs that represent the most valuable IOAs threat hunters can investigate. TTPs provide insight into the motivations and behaviors of a threat actor.
- Tactics describe what the adversary seeks to accomplish. Tactics might include initial access, privilege escalation, credential access, lateral movement, and impact.
- Techniques describe how the attacker seeks to accomplish the objective of the tactic they’re using and can provide deeper insight into the overarching tactic. For example, to achieve the tactic of credential access, an attacker might use a technique like stealing or forging Kerberos tickets.
- Procedures are the more detailed steps laddering up to the techniques attackers use to perform a tactic. To continue the example, in order to steal credentials, a hacker might utilize a Golden Ticket attack.
Pyramid of Pain: Coined by David Bianco, the Pyramid of Pain provides a hierarchy of indicators that threat actors leave behind during an attack. The pyramid demonstrates that IOCs are less valuable than IOAs with TTPs being the most valuable indicators that threat hunters can leverage in tracking down an adversary.
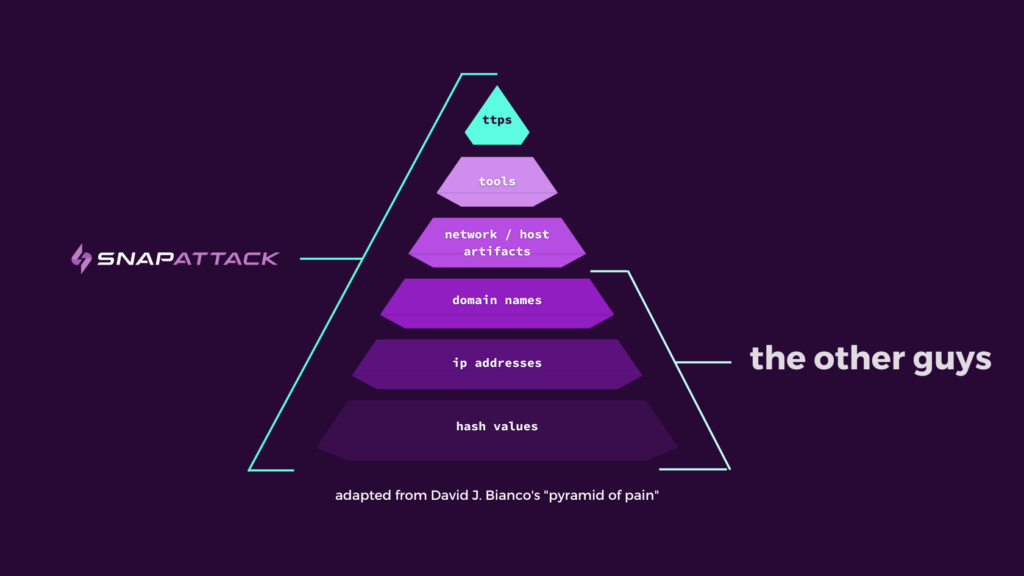
SnapAttack empowers security teams to hunt threats with indicators that ladder all the way to the top of the pyramid of pain.
Trigger: A trigger is the event that kicks off a threat hunt. It points threat hunters to an abnormality or malicious activity in their network that’s cause for alarm bells to start ringing.
Investigation: The investigation is the threat hunt that follows the trigger, wherein hunters equip tools to detect and research the activity at hand.
At the conclusion of the investigation, hunters can determine whether the suspicious activity was truly malicious or simply a false alarm.
Response: If the activity was malicious, the threat hunter will communicate those findings and any relevant information to their security teams so they can craft and execute an appropriate response.
Regardless of their findings, whether the threat was present or not, the data they captured contributes to the larger image of the organization’s security landscape as a whole.
SnapAttack cuts the threat detection development lifecycle from days to minutes. Learn how you can do the same with our recent eBook, Streamlining the Threat Detection Development Lifecycle with SnapAttack.
Cyber Threat Hunting Tools
To successfully research, investigate, and respond to threats, security teams will invest in many monitoring, detection, and response tools.
Logs: A log is a maintained record of all events that occur in a network. While log events themselves are completely normal, any abnormal or unusual log entries can serve as a red flag for threat hunters as they examine network data.
Threat intelligence: Threat intelligence feeds are the basis of much of a threat hunter’s research. Working in tandem with network monitoring tools like SIEM and EDR, teams can contextualize alerts as they come in to appropriately prioritize them and respond.
Staying up to date on emerging threat intelligence is crucial for proactive threat hunters looking to stay ahead of impending attacks and adversaries.
Network monitoring tools (SIEM, EDR/XDR, IDS/IPS): Tools like SIEM, EDR, IDS/IPS, and XDR are more traditional threat detection tools that many organizations rely on when they don’t have the capacity for a threat hunting team – but they still provide a useful starting point for threat hunters.
- SIEM (Security Information and Event Management) tools maintain log data and collect IOCs for hunters to pursue.
- IDS (Intrusion Detection Systems) and IPS (Intrusion Protection Systems) follow the same vein and identify malicious behavior as it occurs so security teams can stop attackers in their tracks.
- EDR (Endpoint Detection and Response) monitors endpoint activity and records any suspicious events; XDR (its more advanced counterpart) takes these capabilities a step further with detection and response across not only endpoints but networks, SIEM, servers, and other data sources.
Home lab: A home lab is a simulated, smaller-scale version of a business’ network. By utilizing various types of technology and equipment, threat hunters can build an at-home version of a true enterprise environment. Cybersecurity professionals build and test on home labs to emulate a realistic organizational threat landscape and further hone their craft.
Not only will a home lab give threat hunters their own simulated environment to take their work from practice to perfect…but to build a home lab requires a deep understanding of IT infrastructure and their organization’s threat landscape.
Developing this understanding and continuously honing the skills they’ll need in a real-world attack scenario displays initiative and strengthens those threat hunting muscles – even when they’re off the clock.
SnapAttack’s no-code detection builder and universal detection translator empower security teams to build and deploy detections in any coding language, no coding knowledge required. SnapAttack subscribers can try both features out now.
Cyber Threat Hunting Frameworks
There are several approaches threat hunters can take to their investigation. There is no one true path to threat hunting, nor is there one framework that will always triumph over the others – different adversaries, situations, and organizations call for different approaches to threat hunting.
Reactive Threat Hunting Frameworks
Reactive threat hunting occurs when a threat hunter is investigating historical events or past IOCs in their network.
1. Trigger-based / historical events: The first threat hunting framework is trigger-based threat hunting. As the name implies, it’s a reactive method wherein threat hunters investigate a threat following a malicious event.
2. Threat intelligence-based: Another reactive threat hunting framework is intelligence-based hunting. Threat hunters leverage insights from threat intelligence feeds and monitoring tools to react to IOCs present in the network.
Proactive Threat Hunting Frameworks
When they have the time and space, security teams should employ a proactive approach – getting ahead of the threat sets teams up to stay ahead of the threat.
1. Hypothesis-based: Pivoting towards a proactive threat hunting model, hypothesis-based threat hunting originates before the malicious activity has taken place. Instead, teams will develop a hypothesis about their network’s security that’s supported by a thorough assessment of the company’s risks, vulnerabilities, and overall security standing.
2. Hunting IOAs and TTPs: IOAs and TTPs are the most proactive artifacts that threat hunters can leverage in a hunt. Since they’re occurring in real-time, hunting for IOAs and TTPs means that adversaries are identified and shut down before any damage is done. Once threat hunters have determined the IOAs and TTPs that have potential to damage their organization, they begin the hunt to prevent attacks from occurring in the first place.
Check out our recent blog about proactive threat hunting at scale to stay ahead of the threat.
Cyber Threat Hunter Traits
The foundation for a promising threat hunter starts long before the skills, tools, and technical experience needs to take root – it starts with personality and soft skills.
Threat Hunter Trait #1: Independence + Drive
Threat hunting is a largely independent activity with a great deal of time spent flying solo. Threat hunters need the initiative and self-determination to seek out hidden threats and investigate them on their own.
Threat Hunter Trait #2: Communication + Collaboration
Though it may seem contradictory to the point above, threat hunters still need to have a team player mindset backed up with stellar communication skills.
Though they’re highly technical, threat hunters must communicate their findings to a group that’s the complete opposite: stakeholders like SOC managers, CISOs, and other leaders in their organization. They also need to be comfortable stepping into a team setting to work with other analysts and threat hunters to detect and remediate threats.
Threat Hunter Trait #2: Curiosity + Enterprise Awareness
The road to becoming a cyber threat hunter is never really complete. What takes a security professional the extra mile is an endless curiosity to continue learning every day.
This might look like using a home lab, consistently researching emergent threats and cybersecurity trends, or diligently keeping up with organizational shifts that can affect their threat landscape. Most of the time, a combination is the mark of a born threat hunter.
Check out our webinar replay, “The Art + Science of Pre-Crime Threat Hunting” to break the killchain earlier with proactive threat hunting.
Cyber Threat Hunter Skills
On the more technical side, threat hunting is a sophisticated, complicated discipline – there are some hard skills that security professionals will need to master (or at least build a foundation in) before they can attain the title of “threat hunter”.
Threat Hunting Skill #1: Programming / Coding
Depending on the coding languages their organization uses, cyber threat hunters need to be fluent in at least one programming or scripting language. That said, the more the merrier – they’ll likely need to work across various complex environments and networks in their tenure as a threat hunter.
Threat Hunting Skill #2: Data Analysis + Reporting
Making their findings actionable for leadership means turning them into digestible, tangible figures – something CISOs, board members, SOC managers, and other stakeholders can understand. Threat hunters must be able to analyze data and then turn it into visual, meaningful metrics and diagrams that communicate next steps and priorities to a non-technical crowd.
SnapAttack provides security leaders with clarity and confidence with reports that map to the MITRE ATT&CK matrix and other key metrics in a SOC.
Threat Hunting Skill #3: Pattern Recognition
Much of threat hunting is reliant on identifying suspicious activity in a network – and to know what’s suspicious, threat hunters must first know what’s normal.
They need a comprehensive understanding of typical behavior in their network and a keen eye to recognize patterns of what’s not. Recurring patterns can illuminate behaviors of adversaries as many attacks spawn from the same initial activity, like the deployment of malware.
Threat Hunting Skill #4: Data Forensics
Experience in data forensics provides a foundation in incident response that can be extremely valuable to a threat hunter. Threat hunters will need to analyze files for suspicious activity that might not be immediately obvious to the untrained eye. Having worked in digital forensics, threat hunters learn what questionable activity looks like and how to go about seeking it out.
AI and machine learning are revolutionizing the threat landscape and how we fend off attackers. Check out our blog, “Enabling Effective Threat Detection Through Data Science” to learn more.
Who Makes a Good Threat Hunter?
When you’re looking to level up a member of your team, it’s important to think about the foundational skill set and experience you’d like them to start out with.
Threat Hunter Candidate #1: SOC Analysts
With perhaps the most directly applicable experience, SOC analysts are the reactive counterpart to the proactive threat hunter. SOC analysts triage incoming alerts from detection tools like SIEMs and EDRs in search of attack behaviors. With curiosity, seat time, and honed intuition, analysts can gain the skill of pattern identification that is so critical for successful threat hunting.
Making that transition from SOC analyst to threat hunter means a shift from triaging incoming alerts from rules detecting known threats, to instead researching and tracking down the harder-to-find indicators of attack. Where SOC analysts analyze alerts coming in from data streams like logs, SIEMs, and other network analysis tools, threat hunters actively search for threats before they’ve received those alerts.
Threat Hunter Candidate #2: CTI Analysts
Another role well-equipped for the threat hunter route is the cyber threat intelligence (CTI) analyst. Though CTI analysts don’t typically have as much technical experience – they’re more focused on the reporting, briefing, and communicating of emergent threats against an organization – they have a strong understanding of relevant threats and have the information at their fingertips to understand those threats deeply.
This means, with the development of the requisite technical skills, they can become well-versed in what to look out for when it comes to vulnerabilities, suspicious activity, and hunting down adversaries.
Threat Hunter Candidate #3: Red Teamers / Offensive Testers
Findings from red team engagements are used to determine the larger security strategy within the SOC, pointing hunters and analysts towards their most pressing vulnerabilities.
Offensive testers have a unique perspective that’s extremely valuable to a rising threat hunter: they know how to think like a hacker. And when you’re hunting down hackers, there’s no better approach than to step into their shoes. The complexity in pivoting from red to blue comes from translating their skills in covering their tracks in a red team engagement, to finding those same footprints an adversary is likely to leave behind.
Threat Hunter Candidate #4: Detection Engineers
Threat hunters’ findings inform the detections that make up an organization’s response or preparation against a present threat. The skillset of a detection engineer is the very closely aligned to that of a threat hunter.
Working on the other side of threat detection – the development of detection strategies, creation of and deployment of detections – is another unique perspective that can benefit threat hunters. It gives them the context for what the detection engineers will need to know after an investigation has come to a close and it’s time to formulate a response.
Threat Hunter Candidate #5: Incident Responders
Incident responders are adept at following the trail of breadcrumbs that lead back to an incident’s early stages as well as the sequence of events the adversary used to accomplish their attack objective. The role is inherently reactive in nature, and the responders are usually only called in when the horse has left the barn.
Their skills are directly applicable to the proactive threat hunt mission, and organizations that can find time between incidents should be tasking their incident responders in proactive hunts. The biggest obstacle here? Like many roles on security teams, time.
Adopt threat-informed defense in your threat detection with our webinar replay, “Demystifying the Tradecraft of Threat-Informed Defense”.
Conclusion: Level Up a Threat Hunter
Before looking outward in your search to enhance your security posture, it’s worth taking a look at your existing team. In the thick of both the growing talent gap and worsening threat landscape, the efficiency of your security team has never been more crucial. With the right preparation and foundation, security analysts of all kinds can achieve the role of “threat hunter” to make their team more proactive and advanced.
SnapAttack is a threat management platform built by threat hunters, CISOs, and SOC leaders, and threat hunters for threat hunters, CISOs, and SOC leaders.
SnapAttack includes threat hunting and training capabilities that don’t just streamline threat hunts for your advanced team members – they make it quick and easy for your most junior analysts to level up their skillset to the caliber of a threat hunter.
Book a meeting now to find out how you can empower the teams you already have to stay ahead of the threat with the tools you already own.




