proof of value
See SnapAttack in action, in your own hands.
Experience SnapAttack’s platform firsthand. Get a free, 30-day proof of value and discover how SnapAttack can benefit your organization.
how it works
How Our POV Process Works
Book a demo and discover the value our customers experience—tailored to your practice!
Define the goals
We’ll get everything we need to ensure a smooth POV process:
Scope out the integrations
Define the use cases + success criteria
Map out a timeline
Understand who will be involved
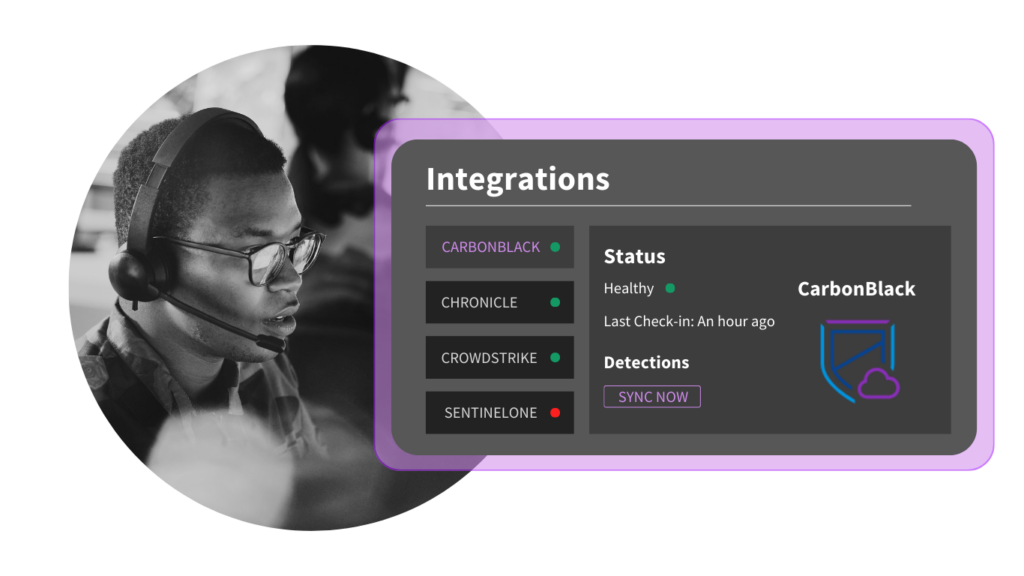
Get set up
We’ll get you all set up to begin the onboarding process:
Provision users
Configure integrations with ease
Hold kick-off call
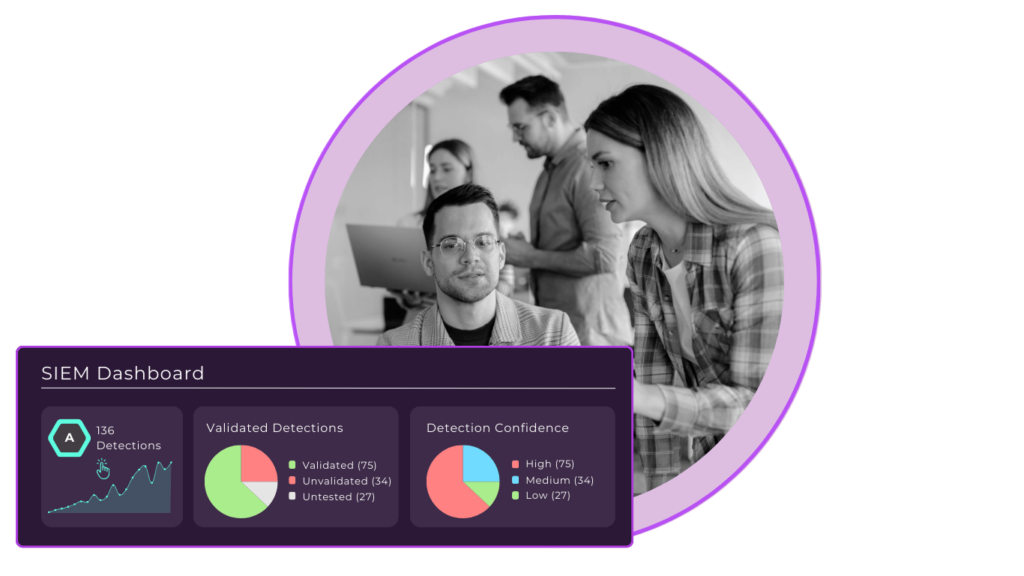
Get hands on support as you learn the platform
With our evaluation, your teams will understand more than just how to use the tool, they’ll also get:
Weekly hands-on workshops with a dedicated SnapAttack SME for feedback, Q&A, and use case exploration
Full access to the platform and unlimited users, for self-paced evaluation
Ad-hoc 1:1 sessions with your SnapAttack SME for technical support, Q&A, and deep dives into complex threat detection topics
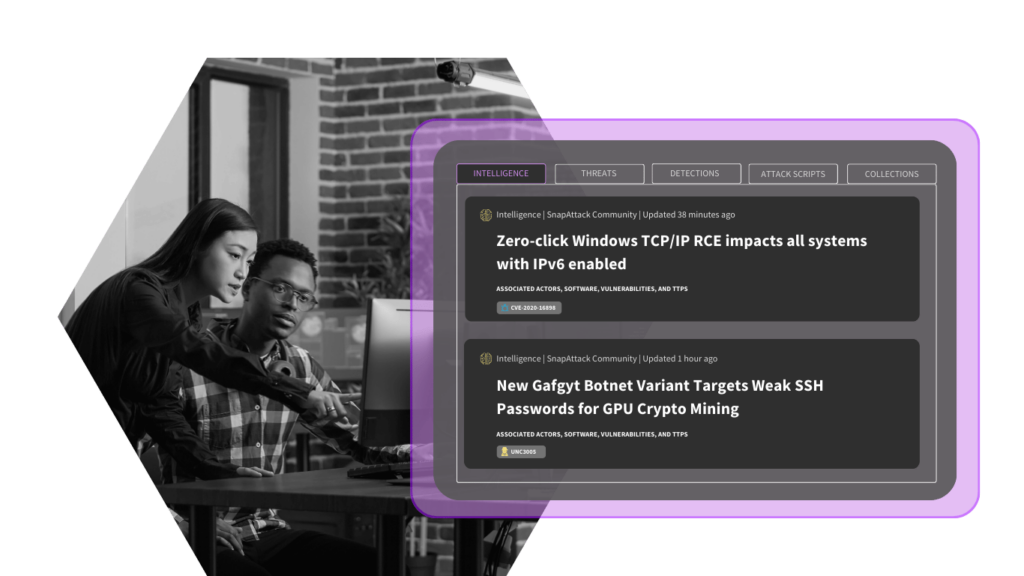
Measure the value delivered
We’ll review the outcomes that were delivered during the POV, assess how the outcomes align with the success criteria initially set, and ultimately decide if we’re a good solution for your use cases.
From there, you can decide if SnapAttack is the right fit for your organization.
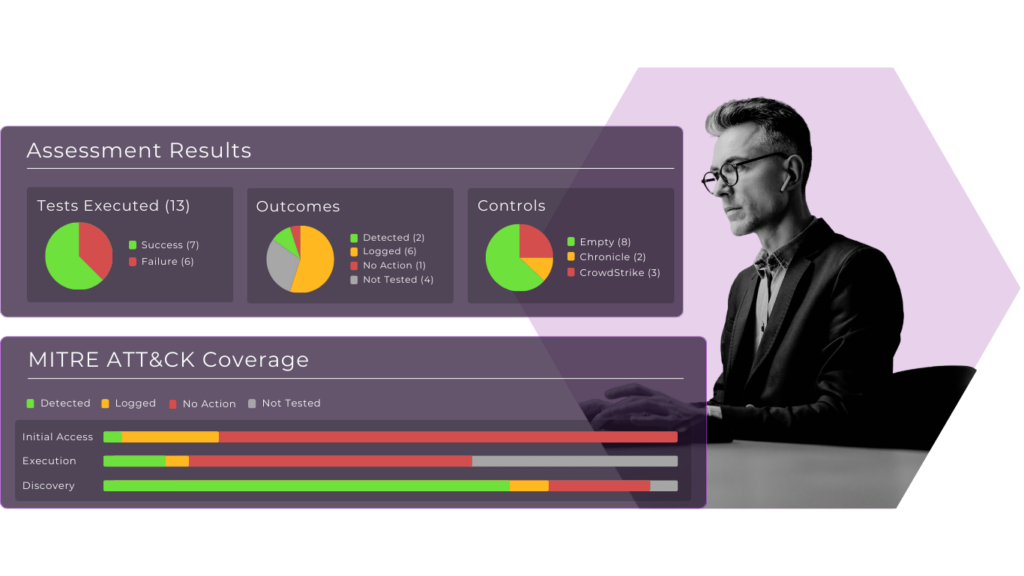
why snapattack?
Why SnapAttack's POV?
Deliver measurable value (on your terms).
Every company is different and SnapAttack may not be for everyone. Before we implement anything, we work with you to understand the fit, identify a specific use case, and identify the path to real, measurable value. We’ll even help you articulate the value to higher ups.
Get hands-on guidance for every single user.
No generic onboarding videos / one-size fits all tutorials. We provide dedicated hands-on guidance and support to show each and every user how SnapAttack works, how to use it, and how to get value from SnapAttack.
Start deploying detections in a matter of minutes.
No lengthy implementation processes. Onboard and integrate in as quickly as 1 day. Get unlimited access to the platform for unlimited users throughout the entire duration of the POV, and significantly improve detection capability in just a few days.
Try before you try.
Users get full and complete access to the platform during the POV so that they can see the value of our platform, exactly the same way that a customer would.
Receive complimentary reporting.
Our reporting includes:
• Threat Priority Reports: Which threats are the most urgent?
• MITRE ATT&CK Reporting: Measure your coverage before and after SnapAttack.
Get support from cybersecurity experts.
Our team is compromised of the best in the business, so you can receive top-notch support during the POV process:
• Dedicated SnapAttack SME
• Direct Slack / Teams Access
• 1-on-1 Ad-Hoc Calls for Anything



professional services
Need a hand growing your threat detection capabilities even faster with fewer resources? Check out our add-on professional services.
threat hunting-as-a-service
Proactively reduce risk across your attack surface – even within large, decentralized environments.
detection engineering-as-a-service
Deploy rapid detection coverage for the threats that matter most.
mitre att&ck mapping assessment
Operationalize expert threat research that’s actually relevant to your organization.
siem migration support
Get up and running quickly in your new SIEM with our seamless migration capabilities.

SnapAttack delivers value by making threat detection easy and efficient.
“It’s great to have a platform like SnapAttack that’s so easy to demonstrate. The flow is seamless, and not many tools can nail that.”
SnapAttack Customer
learn more
Frequently Asked Questions (FAQs)
You can expect to have the opportunity to explore Threat Hunting and Detection Engineering use cases in-depth with help of expert resources from SnapAttack, test and evaluate any features and functions that interest you and are relevant to your use cases, and generally use the solution to detect the threats that matter, faster and easier.
A typical POV lasts anywhere from 2 to 4 weeks, depending on your availability, number, and complexity of use cases. Ad-hoc meetings can always be scheduled in-between existing meetings with your SnapAttack Solutions Architect to tackle specific challenges or explore specific topics in greater depth.
When conducting a POV, there are several hard requirements and a few soft (recommended) requirements.
Hard Requirements
Operational:
- Commit resources & time to POV
- Develop success criteria with SnapAttack
Technical
- Scope at least 1 SIEM with endpoint data OR 1 EDR where translation support in SnapAttack is available
Soft Requirements
Technical
- At least 1 SIEM with endpoint data or 1 EDR where full integration (search/deploy) support in SnapAttack is available
- Existing SIEM rules mapped to MITRE ATT&CK and exported in a machine-readable format (CSV, JSON, TXT)
If you have an extremely small or resource limited team, a “standard” POV may not be suitable for you. However, SnapAttack offers several services that enables them to effectively operate the platform for you in a Detection Engineering and/or Threat Hunting capacity. Reach out to your SnapAttack representative for more information.
Splunk, Azure Sentinel, SentinelOne, Chronicle, MDE, LogScale, Carbon Black, and Elastic
The platform can be used without a full integration; however, some features and functions will not be available.
SnapAttack offers a MITRE ATT&CK Technique Assessment service that helps customers map detections to applicable techniques and sub-techniques. However, this service offering is only available after the POV has concluded and a purchase has been made.
The integration process is typically very fast and low-lift, but varies between technologies. Generally, configuring the integration takes a few minutes. However, some SIEMs/EDRs require installation of applications, provisioning of permissions, or reaching out to vendor support for API keys/tokens. Depending on who owns the applications, change control processes, and vendor responsiveness, this process can take longer.

